Message Digest in Information security - GeeksforGeeks
A Computer Science portal for geeks. It contains well written, well thought and well explained computer science and programming articles, quizzes and practice/competitive programming/company interview Questions.
A computer science portal for geeks. It contains well written, well thought and well explained computer science and programming articles, quizzes and practice/competitive programming/company interview Questions.
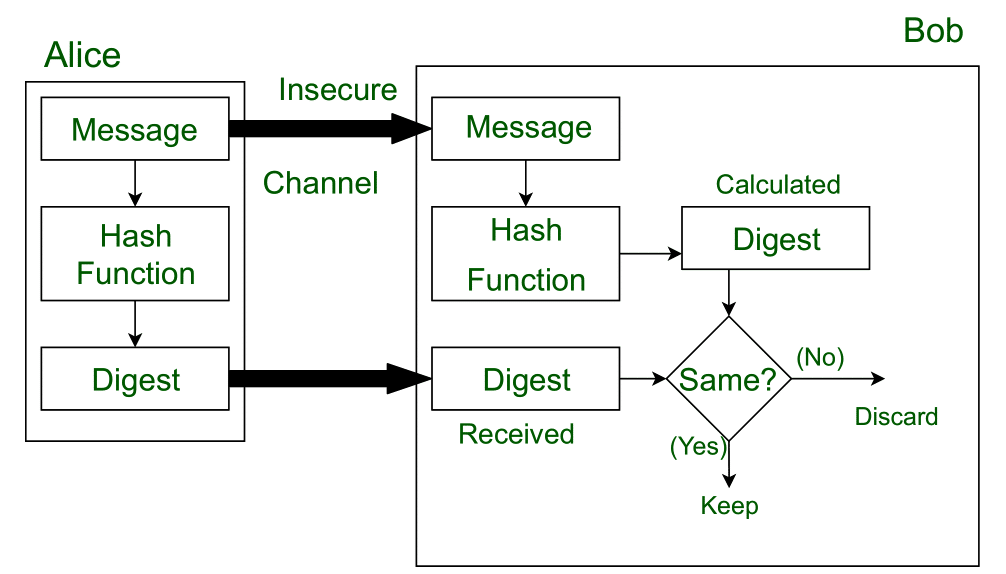
Message Digest is used to ensure the integrity of a message transmitted over an insecure channel where the content of the message can be changed . The message is passed through a Cryptographic hash function. This function creates a compressed image of the message called Digest. Lets assume Alice sent a
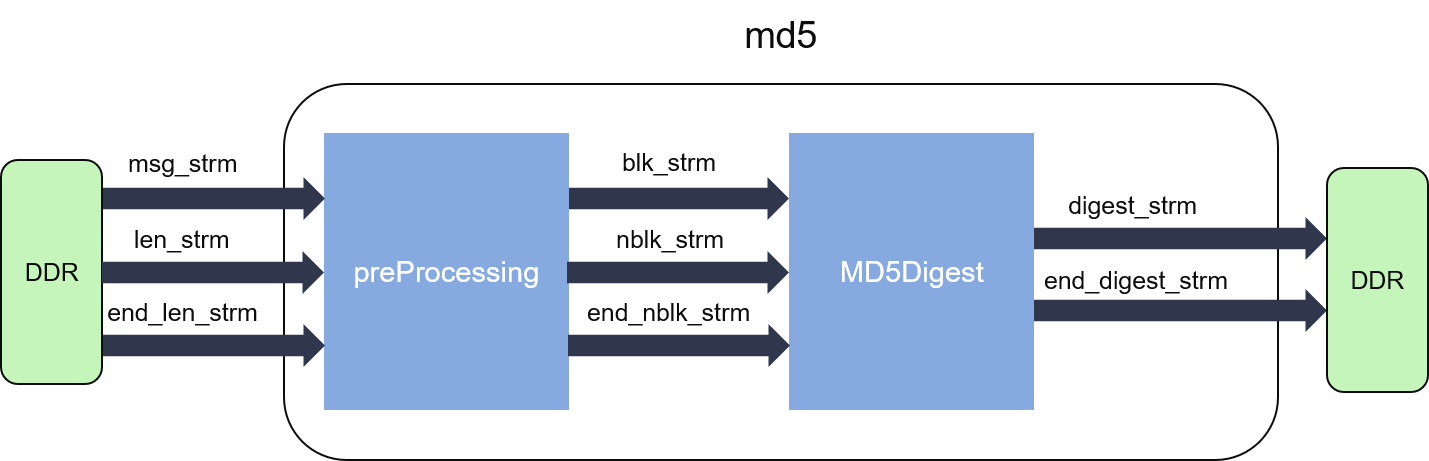
The MD4/MD5 Message-Digest Algorithms

GeeksforGeeks LPU
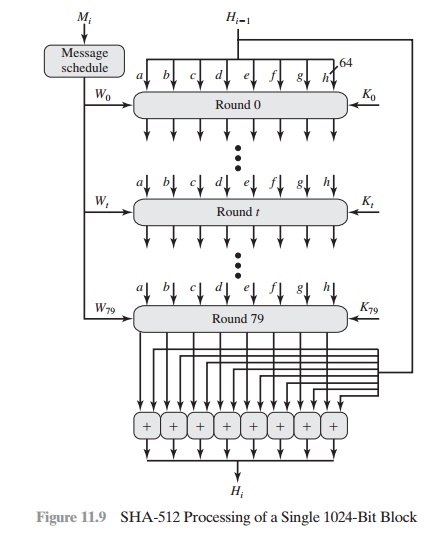
Secure Hash Algorithm (SHA)
CRYPTOGRAPHY (2).pdf
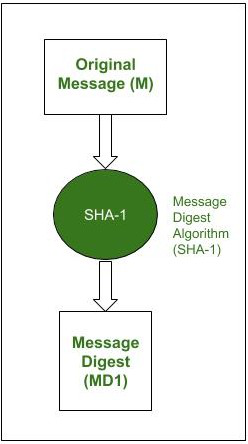
RSA and Digital Signatures - GeeksforGeeks
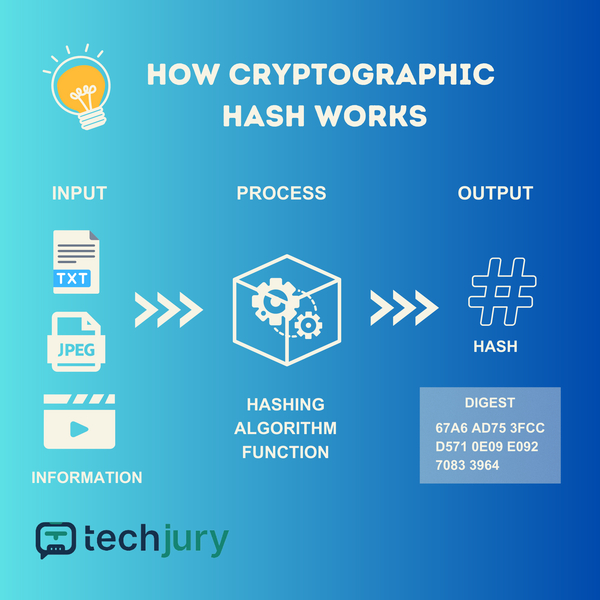
What Is Cryptographic Hash? [A Beginner's Guide]

message digest generation in cryptography –
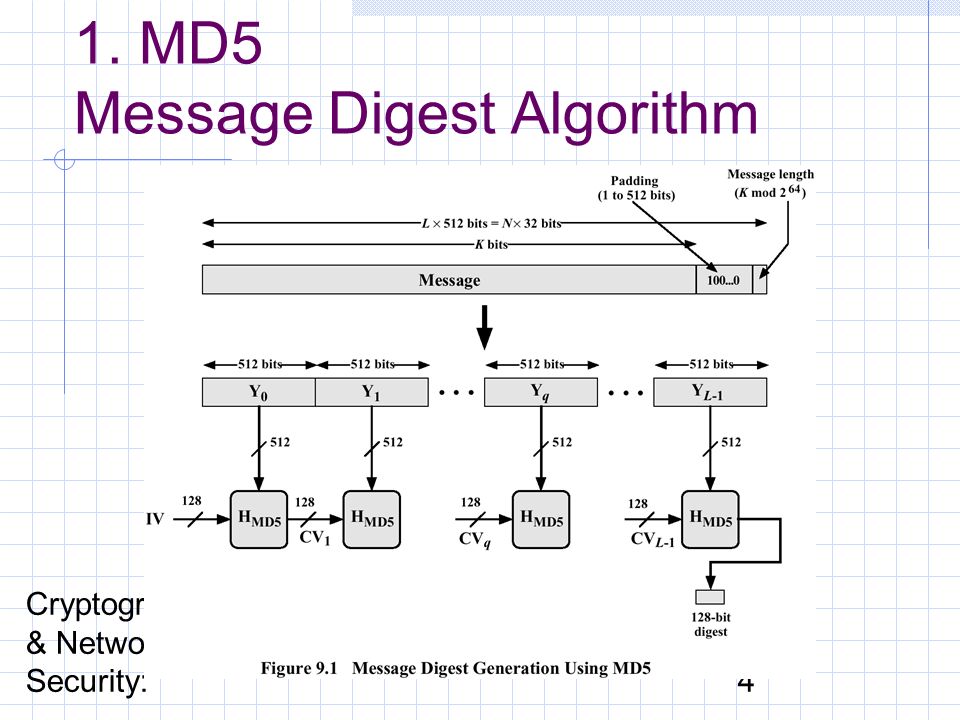
Cryptography & Network Security: 1 IX. Hash Algorithms Look at

Use 6 Cryptographic Hash Functions in Your Next Mule application
MD5 Hash Algorithm in Cryptography: Here's Everything You Should Know

PDF) Cryptography Algorithm Gaurav Chhikara

Basics of Cryptographic Primitives for Blockchain Development
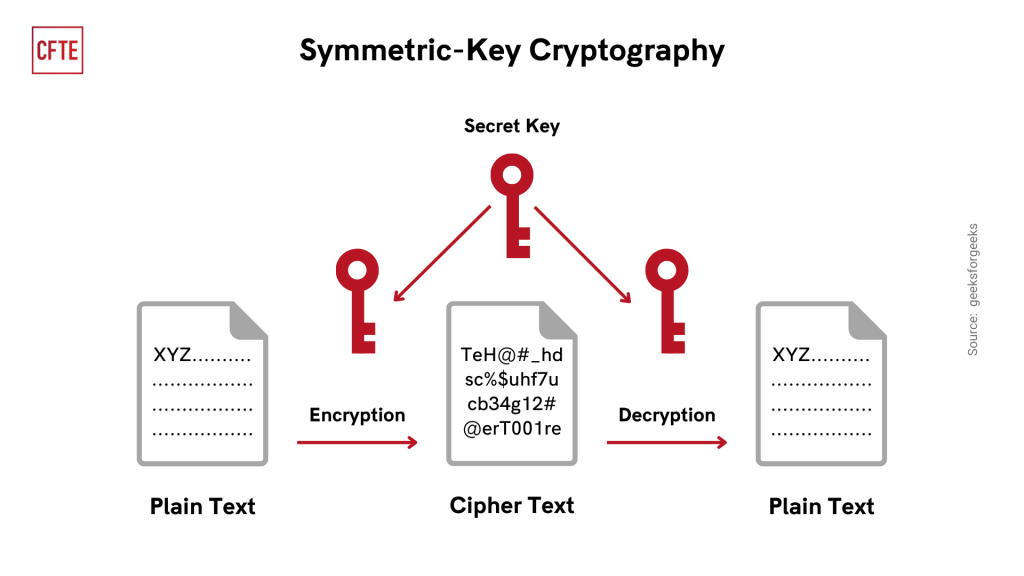
What is Cryptography in Blockchain? How Does it Work? - CFTE